[312-50V12 Exam Must See] 312-50V12 Dumps 2023 Practice Questions Update

Today, let’s talk about how to pass the certification 312-50v12 exam.
In the process of learning, the first very important factor is not to blind yourself all at once, that is, do not think of eating a fat person in one go. For example, instead of brushing up on practice questions at the beginning, you need to sink down and learn some basic theoretical knowledge of the Certified Ethical Hacker Exam (CEHv12).
Later, you need to find reliable 312-50V12 dumps and then practice. This is the correct order to pass the CEHv12 exam.
Download the latest 312-50v12 dumps: https://www.pass4itsure.com/312-50v12.html (528 new practice questions).
Steps to correctly pass the 312-50V12 exam, do you understand?
Remember the first step? Master the basics of the CEHv12 exam.
The 312-50v12 exam refers to the EC-Council Certified Ethical Hacker (CEH) v12 certification exam. The exam mainly covers the following:
- Cybersecurity basics
- Network scanning techniques and tools
- Vulnerability scanning and vulnerability assessment
- Penetration testing methodology
- Social engineering
- Web application attacks
- SQL injection attacks
- Wireless network security
- Mobile device security
- Cloud computing security
These are the points you need to master.
What is the second step? Select the 312-50v12 dumps of the pair.
Preparing for the 312-50V12 exam requires systematic and targeted practice questions, which Pass4itSure can do.
The updated 312-50V12 dumps can help candidates allocate time and energy reasonably, fully grasp the knowledge points and skills required by the exam, and reduce the risk of exam failure.
Therefore, the Pass4itSure 312-50V12 dumps are your ideal choice to pass the Certified Ethical Hacker exam (CEHv12).
What’s next, it’s practice, practice. If you just read a book, you can’t learn.
Bring you the latest 312-50v12 practice questions, from the latest dumps, you can participate.
312-50V12 Free Dumps Practice Questions 2023
Question 1:
Mike, a security engineer, was recently hired by BigFox Ltd. The company recently experienced disastrous DoS attacks. The management had instructed Mike to build defensive strategies for the company\’s IT infrastructure to thwart DoS/ DDoS attacks. Mike deployed some countermeasures to handle jamming and scrambling attacks.
What is the countermeasure Mike applied to defend against jamming and scrambling attacks?
A. Allow the usage of functions such as gets and strcpy
B. Allow the transmission of all types of addressed packets at the ISP level
C. Implement cognitive radios in the physical layer
D. A Disable TCP SYN cookie protection
Correct Answer: D
Question 2:
John wants to send Marie an email that includes sensitive information, and he does not trust the network that he is connected to.
Marie gives him the idea of using PGP. What should John do to communicate correctly using this type of encryption?
A. Use his own public key to encrypt the message.
B. Use Marie\’s public key to encrypt the message.
C. Use his own private key to encrypt the message.
D. Use Marie\’s private key to encrypt the message.
Correct Answer: B
When a user encrypts plaintext with PGP, PGP first compresses the plaintext. The session key works with a very secure, fast conventional encryption algorithm to encrypt the plaintext; the result is ciphertext. Once the data is encrypted, the session key is then encrypted to the recipient\’s public key
Question 3:
During a recent security assessment, you discover the organization has one Domain Name Server (DNS) in a Demilitarized Zone (DMZ) and a second DNS server on the internal network.
What is this type of DNS configuration commonly called?
A. DynDNS
B. DNS Scheme
C. DNSSEC
D. Split DNS
Correct Answer: D
Question 4:
Ethical backer Jane Doe is attempting to crack the password of the head of its department of ABC company. She Is utilizing a rainbow table and notices upon entering a password that extra characters are added to the password after submitting.
What countermeasure is the company using to protect against rainbow tables?
A. Password key hashing
B. Password salting
C. Password hashing
D. Account lockout
Correct Answer: B
Passwords are usually delineated as “hashed and salted”. salting is simply the addition of a unique, random string of characters renowned solely to the site to every parole before it\’s hashed, typically this “salt” is placed in front of each password. The salt value needs to be held on by the site, which means typically sites use the same salt for each parole.
This makes it less effective than if individual salts are used. The use of unique salts means that common passwords are shared by multiple users. like “123456” or “password”? Aren’t revealed when one such hashed password is known? because despite the passwords being the same the immediate and hashed values are not.
Large salts also protect against certain methods of attack on hashes, including rainbow tables or logs of hashed passwords previously broken. Both hashing and salting may be repeated more than once to increase the issue of breaking the security.
Question 5:
Bob, a system administrator at TPNQM SA, concluded one day that a DMZ is not needed if he properly configures the firewall to allow access just to servers/ports, which can have direct internet access, and block access to workstations.
Bob also concluded that DMZ makes sense just when a stateful firewall is available, which is not the case with TPNQM SA.
In this context, what can you say?
A. Bob can be right since DMZ does not make sense when combined with stateless firewalls
B. Bob is partially right. He does not need to separate networks if he can create rules by destination IPs, one by one
C. Bob is totally wrong. DMZ is always relevant when the company has internet servers and workstations
D. Bob is partially right. DMZ does not make sense when a stateless firewall is available
Correct Answer: C
Question 6:
Which of the following is a command line packet analyzer similar to GUI-based Wireshark?
A. nessus
B. tcpdump
C. ethereal
D. jack the Ripper
Correct Answer: B
Tcpdump is a data-network packet analyzer computer program that runs under a command-line interface. It allows the user to display TCP/IP and other packets being transmitted or received over a network to which the computer is attached.
Distributed under the BSD license, tcpdump is free software.
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software, communications protocol development, and education.
NOTE: Wireshark is very similar to tcpdump, but has a graphical front-end, plus some integrated sorting and filtering options.
Question 7:
what firewall evasion scanning technique makes use of a zombie system that has low network activity as well as its fragment identification numbers?
A. Decoy scanning
B. Packet fragmentation scanning
C. Spoof source address scanning
D. Idle scanning
Correct Answer: D
Question 8:
Ron, a security professional, was pen-testing web applications and SaaS platforms used by his company. While testing, he found a vulnerability that allows hackers to gain unauthorized access to API objects and perform actions such as viewing, updating, and deleting sensitive data of the company.
What is the API vulnerability revealed in the above scenario?
A. Code injections
B. Improper use of CORS
C. No ABAC validation
D. Business logic flaws
Correct Answer: B
Question 9:
An attacker with access to the inside network of a small company launches a successful STP manipulation attack. What will he do next?
A. He will create a SPAN entry on the spoofed root bridge and redirect traffic to his computer.
B. He will activate OSPF on the spoofed root bridge.
C. He will repeat this action so that it escalates to a DoS attack.
D. He will repeat the same attack against all L2 switches of the network.
Correct Answer: A
Question 10:
In an attempt to damage the reputation of a competitor organization, Hailey, a professional hacker, gathers a list of employee and client email addresses and other related information by using various search engines, social networking sites, and web-spidering tools.
In this process, she also uses an automated tool to gather a list of words from the target website to further perform a brute-force attack on the previously gathered email addresses.
What is the tool used by Hailey for gathering a list of words from the target website?
A. Shadowsocks
B. CeWL
C. Psiphon
D. Orbot
Correct Answer: B
Question 11:
Under what conditions does a secondary name server request a zone transfer from a primary name server?
A. When a primary SOA is higher that a secondary SOA
B. When a secondary SOA is higher that a primary SOA
C. When a primary name server has had its service restarted
D. When a secondary name server has had its service restarted
E. When the TTL falls to zero
Correct Answer: A
Question 12:
A new wireless client is configured to join an 802.11 network. This client uses the same hardware and software as many of the other clients on the network. The client can see the network, but cannot connect. A wireless packet sniffer shows
that the Wireless Access Point (WAP) is not responding to the association requests being sent by the wireless client.
What is a possible source of this problem?
A. The WAP does not recognize the client\’s MAC address
B. The client cannot see the SSID of the wireless network
C. Client is configured for the wrong channel
D. The wireless client is not configured to use DHCP
Correct Answer: A
Question 13:
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c
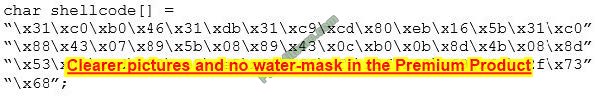
What is the hexadecimal value of NOP instruction?
A. 0x60
B. 0x80
C. 0x70
D. 0x90
Correct Answer: D
Question 14:
Richard, an attacker, aimed to hack loT devices connected to a target network. In this process. Richard recorded the frequency required to share information between connected devices. After obtaining the frequency, he captured the original data when commands were initiated by the connected devices.
Once the original data were collected, he used free tools such as URH to segregate the command sequence. Subsequently, he started injecting the segregated command sequence on the same frequency into the loT network, which repeats the captured signals of the devices.
What Is the type of attack performed by Richard In the above scenario?
A. Side-channel attack
B. Replay attack
C. CrypTanalysis attack
D. Reconnaissance attack
Correct Answer: B
Replay Attacks could be a variety of security attacks on the info sent over a network. In this attack, the hacker or a person with unauthorized access captures the traffic and sends a communication to its original destination, acting because of the original sender.
The receiver feels that it\’s an Associate in Nursing genuine message however it\’s really the message sent by the aggressor. the most feature of the Replay Attack is that the consumer would receive the message double, thence the name, Replay Attack.
Prevention from Replay Attack: 1. Timestamp technique prevention from such attackers is feasible if the timestamp is employed at the side of the info. Supposedly, if the timestamp on information is over a precise limit, it may be discarded, and the sender may be asked to send the info once more.2.
Session key technique nother way of hindrance is by the victimization session key. This key may be used one time (by sender and receiver) per dealing, and can\’t be reused.
Question 15:
Chandler works as a pen-tester in an IT firm in New York. As a part of detecting viruses in the systems, he uses a detection method where the anti-virus executes the malicious codes on a virtual machine to simulate CPU and memory activities. Which type of virus detection method did Chandler use in this context?
A. Heuristic Analysis
B. Code Emulation
C. Scanning
D. Integrity checking
Correct Answer: B
At last:
Remember the correct order of the 312-50V12 exams, which is important to pass the exams, and then download the Pass4itSure latest 312-50V12 dumps https://www.pass4itsure.com/312-50v12.html to practice all 312-50V12 exam questions.
