New CEH-001 Exam Dumps Practice Questions Released, Extremely High Success Rate

New CEH-001 exam dumps practice questions are the best solution for the GAQM certification CEH-001 Exam.
So we updated the new CEH-001 exam dumps in 2024 https://www.pass4itsure.com/ceh-001.html 878+ new practice questions (PDF or VCE) which have been verified by many people and have an extremely high success rate.
CEH-001 exam best solution:
- Make a study plan
- Choose the right learning materials
- Practice exercises
- Join the CEH Forum and watch the blog
- Create a list of learning topics
- Take a mock test
- …
All of them are CEH-001 exam solutions, but none of them are optimal.
Remember, the new CEH-001 exam dumps practice questions are the best solution for the GAQM certification CEH-001 exam.
What kind of exam is CEH-001?
Certified Professional Ethics Hacker (CPEH), aka CPEH-001 exam. A Certified Professional Ethical Hacker (CPEH) ™ is usually hired by organizations that trust him or her to use the same methods used by hackers to try to infiltrate networks and/or computer systems to find and fix computer security vulnerabilities.
Exams are both online and proctored exams. The exam consists of 100 multiple-choice questions, and you must answer 120 questions correctly within 70 minutes to pass the exam. The Professional Ethics Hacker Certification (CPEH) ™ certificate is valid for life.
The CEH-001 exam is so hot
What words are the most popular and attracted the most attention from the industry in the past two years? The CEH-001 exam can rank in the top three. If you are a professional who understands Certified Ethical Hacker (CEH), you can say that you are the most fragrant one!
Hurry up, here are some free practice questions for you to practice.
New Certified Ethical Hacker (CEH) CEH-001 dumps practice questions shared online
From: Pass4itSure
Several questions: 15/878
Related certifications: GAQM certification
Question 1:
Clive is conducting a pen test and has just port-scanned a system on the network. He has identified the operating system as Linux and has been able to elicit responses from ports 23, 25, and 53. He infers port 23 is running Telnet service, port 25 is running SMTP service, and port 53 is running DNS service. The client confirms these findings and attests to the current availability of the services. When he tries to telnet to port 23 or 25, he gets a blank screen in response. On typing other commands, he sees only blank spaces or underscore symbols on the screen. What are you most likely to infer from this?
A. The services are protected by TCP wrappers
B. There is a honeypot running on the scanned machine
C. An attacker has replaced the services with trojaned ones
D. This indicates that the telnet and SMTP servers have crashed
Correct Answer: A
Question 2:
You want to carry out session hijacking on a remote server. The server and the client are communicating via TCP after a successful TCP three-way handshake. The server has just received packet #120 from the client. The client has a receive window of 200 and the server has a receive window of 250.
Within what range of sequence numbers should a packet, sent by the client fall to be accepted by the server?
A. 200-250
B. 121-371
C. 120-321
D. 121-231 E. 120-370
Correct Answer: B
Question 3:
Which of the following are password-cracking tools? (Choose three.)
A. BTCrack
B. John the Ripper
C. KerbCrack
D. Nikto
E. Cain and Abel
F. Havij
Correct Answer: BCE
Question 4:
You want to use Netcat to generate a huge amount of useless network data continuously for various performance testing between 2 hosts.
Which of the following commands accomplish this?
A. Machine A #yes A | nc 2222 > /dev/null Machine B #yes B | nc machine 2222 > /dev/null
B. Machine A cat some file | nc 2222 Machine B cat some file | nc other machine 2222
C. Machine A nc 1234 | uncompress | tar xvfp Machine B tar cfp – /some/dir | compress | nc 3 machine 1234
D. Machine A while true: do nc 6000 machine 2 Machine B while true; do nc 6000 machine 2 done
Correct Answer: A
Question 5:
Which United States legislation mandates that the Chief Executive Officer (CEO) and the Chief Financial Officer (CFO) must sign statements verifying the completeness and accuracy of financial reports?
A. Sarbanes-Oxley Act (SOX)
B. Gramm-Leach-Bliley Act (GLBA)
C. Fair and Accurate Credit Transactions Act (FACTA)
D. Federal Information Security Management Act (FISMA)
Correct Answer: A
Question 6:
What is the goal of a Denial of Service Attack?
A. Capture files from a remote computer.
B. Render a network or computer incapable of providing normal service.
C. Exploit a weakness in the TCP stack.
D. Execute service at PS 1009.
Correct Answer: B
Question 7:
In TCP communications there are 8 flags; FIN, SYN, RST, PSH, ACK, URG, ECE, and CWR.
These flags have decimal numbers assigned to them:
FIN = 1
SYN = 2 RST = 4 PSH = 8 ACK = 16 URG = 32 ECE = 64 CWR = 128
Jason is the security administrator of ASPEN Communications. He analyzes some traffic using Wireshark and has enabled the following filters.

What is Jason trying to accomplish here?
A. SYN, FIN, URG and PSH
B. SYN, SYN/ACK, ACK
C. RST, PSH/URG, FIN
D. ACK, ACK, SYN, URG
Correct Answer: B
Question 8:
Bob, an Administrator at XYZ was furious when he discovered that his buddy Trent, has launched a session hijack attack against his network, and sniffed on his communication, including administrative tasks such as configuring routers,
firewalls, IDS, via Telnet.
Bob, being an unhappy administrator, seeks your help to assist him in ensuring that attackers such as Trent will not be able to launch a session hijack in XYZ.
Based on the above scenario, please choose which would be your corrective measurement actions. (Choose two)
A. Use encrypted protocols, like those found in the OpenSSH suite.
B. Implement FAT32 filesystem for faster indexing and improved performance.
C. Configure the appropriate spoof rules on gateways (internal and external).
D. Monitor for CRP caches, by using IDS products.
Correct Answer: AC
Question 9:
Why would you consider sending an email to an address that you know does not exist within the company you are performing a Penetration Test for?
A. To determine who is the holder of the root account
B. To perform a DoS
C. To create needless SPAM
D. To illicit a response back that will reveal information about email servers and how they treat undeliverable mail
E. To test for virus protection
Correct Answer: D
Question 10:
Peter is a Linux network admin. As a knowledgeable security consultant, he turns to you to look for help on a firewall. He wants to use Linux as his firewall and use the latest freely available version that is offered. What do you recommend?
Select the best answer.
A. Ipchains
B. Iptables
C. Checkpoint FW for Linux
D. Ipfwadm
Correct Answer: B
Question 11:
Exhibit: Given the following extract from the snort log on a honeypot, what do you infer from the attack?
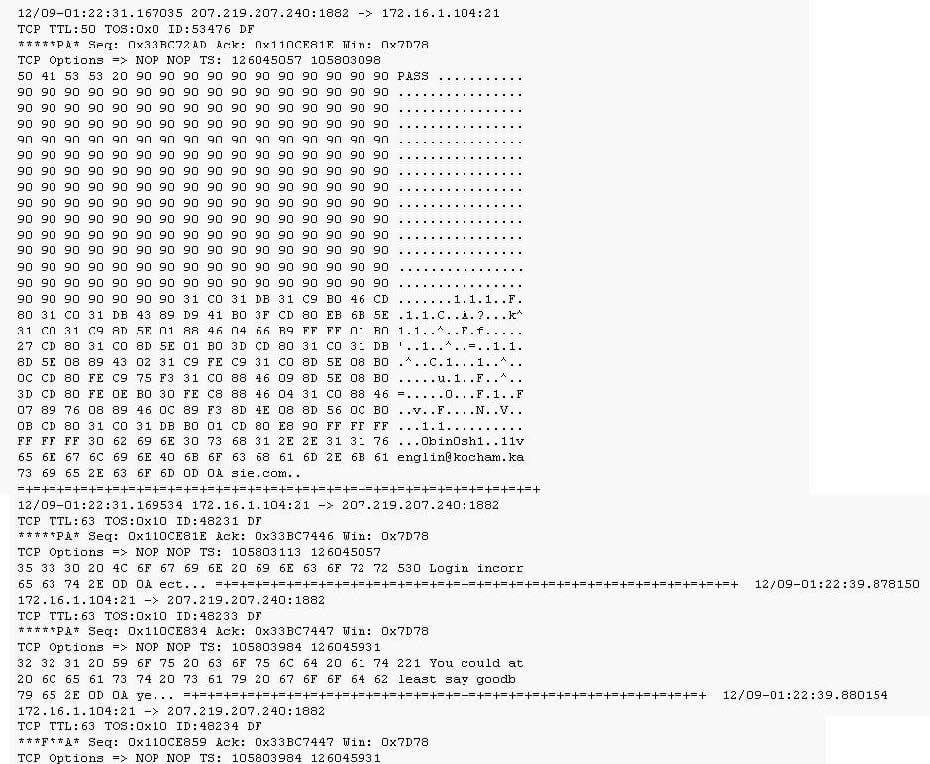
A. A new port was opened
B. A new user id was created
C. The exploit was successful
D. The exploit was not successful
Correct Answer: D
Question 12:
Which cipher encrypts the plain text digit (bit or byte) one by one?
A. Classical cipher
B. Block cipher
C. Modern cipher
D. Stream cipher
Correct Answer: D
Question 13:
Steve scans the network for SNMP-enabled devices. Which port number Steve should scan?
A. 150
B. 161
C. 169
D. 69
Correct Answer: B
Question 14:
This kind of attack will let you assume a user identity at a dynamically generated web page or site:
A. SQL Injection
B. Cross-Site Scripting
C. Session Hijacking
D. Zone Transfer
Correct Answer: B
Question 15:
Jayden is a network administrator for her company. Jayden wants to prevent MAC spoofing on all the Cisco switches in the network. How can she accomplish this?
A. Jayden can use the command. ip binding set.
B. Jayden can use the commanD. No IP spoofing.
C. She should use the command. no DHCP spoofing.
D. She can use the command. ip DHCP snooping binding.
Correct Answer: D
You may also want to ask, are there any good recommendations for Certified Ethical Hacker (CEH) learning resources? Got you!
Useful CEH-001 learning resources new collection (Links are attached)
First of all, you can choose the official GAQM to get useful information.
Again, you can take a look at these books, which are helpful for the exam:
- Certified Ethical Hacker (CEH) Foundation Guide
- CEH certified ethical hacker study guide
- Ceh: Official certified ethical hacker review guide: Exam 312-50
- Certified Ethical Hacker (CEH) Cert Guide: Cert Ethi Hack (CEH Cert Guid
- Certified Ethical Hacker (CEH) Preparation Guide
Of course, there are many good learning resources, so I won’t list them all here.
Is Certified Ethical Hacker (CEH) more worth it or CompTIA Security+?
Both the CompTIA Security+ and CEH certificates are about cybersecurity, but they have a completely different focus. CEH is a more specialized certification, while CompTIA Security+ covers basic cybersecurity knowledge. CompTIA Security+ is for those who are just getting started with cybersecurity.
The two certifications have their characteristics, and the question of whether they are worth it depends on the actual situation of each person. If you’re a newbie, CompTIA Security+ is for you. If you’re looking for something more professional, then CEH has you covered.
Summary:
Today’s world is a competitive world where the brightest, best, and most qualified people work in amazing fields and earn high salaries. Using the new CEH-001 exam dumps practice questions will help you pass the exam, why don’t you try?
Pass4itSure CEH-001 exam dumps https://www.pass4itsure.com/ceh-001.html New practice questions (PDF or VCE) will add success to your exam and help you land amazing new positions.
